
Notes About Some Basics
-
General instruction from Arch wiki.
Dual boot with Windows – ArchWikiDual boot with Windows – ArchWiki Mind that there is no need to create an additional EFI System Partition, since it already exists (see above): when required, mount this to /boot, install your bootloader to it and save the entry in /etc/fstab. read more.
-
Partitioning
Size and tools go to – here
-
Partition table types
If you are installing alongside an existing installation (i.e. dual-booting), a partition table will already be in use. If the devices are not partitioned, or the current partitions table or scheme needs to be changed, you will first have to determine the partition tables (one for each device) in use or to be used.
There are two types of partition table:
- GPT -gpt
- MBR -msdos
Any existing partition table can be identified with the following command for each device:
12# parted /dev/sdx printFor GPT, you are looking for “Partition Table: GPT”. For EFI, you are looking for a small (512 MiB or less) partition with a vfat file system and the boot flag enabled. On it, there should be a directory named “EFI”. If these criteria are met, this is your ESP. Make note of the partition number. You will need to know which one it is, so you can mount it later on while installing GRUB to it.
-
Partitioning tools
For each device to be partitioned, a proper tool must be chosen according to the partition table to be used. Several partitioning tools are provided by the Arch installation medium, including:
parted GPT and MBR fdisk, cfdisk, sfdisk GPT and MBR gdisk, cgdisk, sgdisk GPT - INSTALL ARCHLINUX ON IDEAPAD Y700 some notes on ideapad Y700, http://mkeswani.blogspot.com/2015/12/install-archlinux-on-ideapad-y700.html
- Yet another tutorial with preinstalled windows 8 https://gist.github.com/miguelfrde/5dde43aa08b076106b9e
- Partition Type ID https://en.wikipedia.org/wiki/Partition_type#PID_83h 0x83 native to Linux
-
The best way to detect windows boot mode Most of the linux bootloaders installed for one firmware type cannot launch or chainload bootloaders of other firmware type.
http://www.eightforums.com/tutorials/29504-bios-mode-see-if-windows-boot-uefi-legacy-mode.html
- Boot into Windows
- Press Win key and ’R’ to start the Run dialog
- In the Run dialog type “msinfo32” and press Enter
- In the System Information windows, select System Summary on the left and check the value of BIOS mode item on the right
- If the value is UEFI, Windows boots in UEFI-GPT mode. If the value is Legacy, Windows boots in BIOS-MBR mode.
Prepare Preinstalled Windows
Shrink some space for Linux in Windows
- Make some space for Arch Linux in Windows
-
Win+R and type diskmgmt.msc and hit enter shrink one of the partitions. I also delete the two partitions for reserved for recovery. Want to put a new SSD HD in, I do not have the connecting cable and bracket for the moment.

- Make a bootable installation media for Arch Linux
-
This laptop doesn’t have any CD/DVD drive so the first thing is to make a bootable USB drive.
Boot into Windows 10. In Windows, download archlinux iso from the following website
www.archlinux.org/download
Use the mirror which is closest to you and download the dual iso. archlinux-2015.12.01-dual.iso
Download Rufus from the following location https://rufus.akeo.ie/
Plugin any usb drive/pendrive in your usb port. Make sure that you backup data from this usb drive
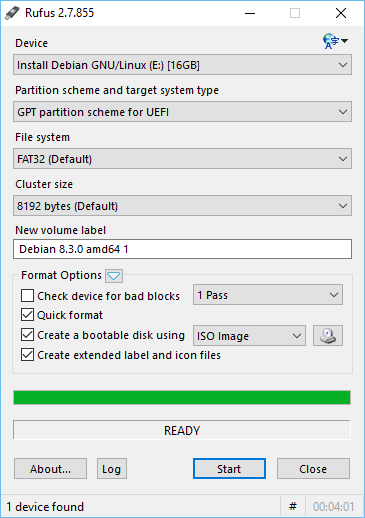
- Attach it to your computer
Turn off Windows fast boot and secure boot
- Shutdown Windows after disabling fast start following instruction here or here. And use the command shutdown -s -t 0 to do so.
-
Restart windows by clicking on Power -> Restart. Make sure that when hitting restart, you are press down Shift key Windows will give you options for Troubleshoot/Adanced Options/UEFI Firmware/
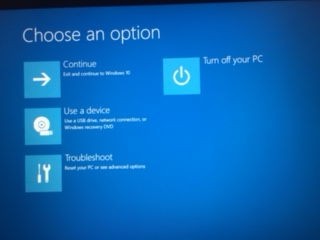
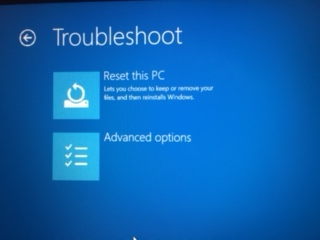
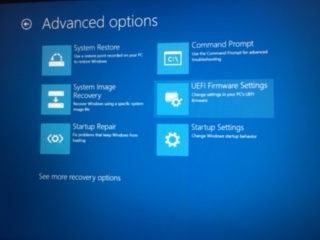
-
Once you restart your machine you should be able to see the BIOS settings.
Under Configuration you should disable Intel Fast boot, disable SecureBoot (more here). Make sure you change the settings for Graphics from Switchable to Internal. This is needed only to install, you can then modify it later. Save the changes and exit.
-
-
Once the machine restarts press and hold F12 key.
This will give you option to boot from various available devices and your USB drive would be one of them
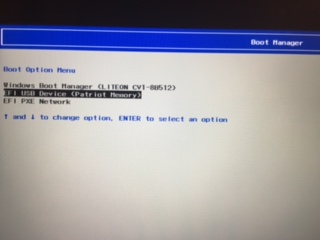
- Select your USB drive to boot
-
Select the UEFI boot mode when you see the ArchLinux boot screen.
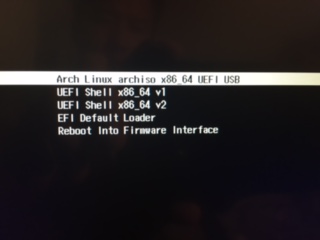
Once the usb has booted you will see the root prompt.
Partition HD with Live CD
Load keyboard layout
$ loadkeys la-latin1
Connect to the internet (Wi-Fi)
|
1 2 3 4 5 |
rfkill unblock wifi # I need to do this for Lenovo Ideapad $ iw dev # Get the interface name $ wifi-menu <wifi_interface_name> ping google.com # check internet |
Creat Partitions for boot, swap and root
- Boot into Arch Linux Installation media in UEFI Mode.
-
Create three partitions in that empty space: (a) boot 200MB (b) Swap 8GB (c) Root Partition
123456789101112131415161718192021gdisk /dev/sdan #Wanna create new partition!#Hit enter, don't care about partition number#Hit enter, automatically first sector will be starting of unallocated space+200MB #Specify the size of the boot partition8300 #Hex code for the Linux boot partition.n #Wanna create new partition!#Hit enter, don't care about partition number#Hit enter, automatically first sector will be starting of unallocated space+8GB #Specify the size of the swap partition8300 #Hex code for the Linux boot partition.n #Wanna create new partition!#Hit enter, don't care about partition number#Hit enter, automatically first sector will be starting of unallocated space#Hit enter, automatically take the rest of space8300 #Hex code for the Linux boot partition.w #Write changes to diskY #Confirm!Type gdisk -l /dev/sda to find out the partition number of theswap partition. In my case, it is 5.The final partition table in my case:
12345678910111213141516$ lsblkNAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTsda 8:0 0 477G 0 disk├─sda1 8:1 0 260M 0 part /boot/efi├─sda2 8:2 0 16M 0 part├─sda3 8:3 0 234.2G 0 part├─sda4 8:4 0 200M 0 part /boot├─sda5 8:5 0 8G 0 part [SWAP]├─sda6 8:6 0 187.1G 0 part│ └─cryptroot 254:0 0 187.1G 0 crypt /├─sda7 8:7 0 25G 0 part├─sda8 8:8 0 1000M 0 part├─sda9 8:9 0 20.2G 0 part└─sda10 8:10 0 1000M 0 part
Encrypt the root partition with LUKS Link
Preparing the disk
chech the info about dm-crypt module
|
1 2 |
modinfo dm-crypt |
dm-cryptwipe on an empty disk or partition
First, create a temporary encrypted container on the partition (sdXY) or the full disk (sdX) you want to encrypt, e.g. using default encryption parameters and a random key via the –key-file /dev/{u}random option (see also Random number generation):
|
1 2 |
# cryptsetup open --type plain /dev/sdXY container --key-file /dev/random |
Second, check it exists
|
1 2 3 4 5 6 |
# fdisk -l ---------------------------------- Disk /dev/mapper/container: 1000 MB, 1000277504 bytes ... Disk /dev/mapper/container does not contain a valid partition table |
Finally, wipe it with pseudorandom (because encrypted) data. A use of if=/dev/urandom is not required as the encryption cipher is used for randomness.
|
1 2 3 |
# dd if=/dev/zero of=/dev/mapper/container status=progress // dd: writing to ‘/dev/mapper/container’: No space left on device |
Preparing non-boot partitions
The following commands create and mount the encrypted root partition. They correspond to the procedure described in detail in Dm-crypt/Encrypting a non-root file system#Partition (which, despite the title, can be applied to root partitions, as long as mkinitcpio and the boot loader are correctly configured). If you want to use particular non-default encryption options (e.g. cipher, key length), see the encryption options before executing the first command:
|
1 2 3 4 5 |
# cryptsetup -y -v luksFormat /dev/sdaX # cryptsetup open /dev/sdaX cryptroot # mkfs -t ext4 -L "Arch Linux" /dev/mapper/cryptroot #or, mkfs.ext4 # mount -t ext4 /dev/mapper/cryptroot /mnt |
Type gdisk -l /dev/sda to find out the partition number of the newly created partition and EFI partition.
Check the mapping works as intended:
|
1 2 3 4 5 |
# umount /mnt # cryptsetup close cryptroot # cryptsetup open /dev/sdaX cryptroot # mount -t ext4 /dev/mapper/cryptroot /mnt |
If you created separate partitions (e.g. /home), these steps have to be adapted and repeated for all of them, except for /boot. See Dm-crypt/Encrypting a non-root file system#Automated unlocking and mounting on how to handle additional partitions at boot.
Note that each blockdevice requires its own passphrase. This may be inconvenient, because it results in a separate passphrase to be input during boot. An alternative is to use a keyfile stored in the system partition to unlock the separate partition via crypttab. See Dm-crypt/Device encryption#Using LUKS to Format Partitions with a Keyfile for instructions.
Prepare Swap partition
|
1 2 3 4 5 |
mkswap -L "Linux Swap" /dev/sda5 #Linux Swap is the label swapon /dev/sda5 #Turn on swap! free -m #Last line will confirm whether swap space has been turned on or not. |
Preparing the boot partition
What you do have to setup is a non-encrypted /boot partition, which is needed for a crypted root. For a standard MBR/non-EFI /boot partition, for example, execute:
|
1 2 3 4 |
# mkfs -t ext4 /dev/sdaY # mkdir /mnt/boot # mount -t ext4 /dev/sdaY /mnt/boot |
Find and mount the efi partition to /mnt/boot/efi
|
1 2 3 4 |
mkdir -p /mnt/boot/efi #Type gdisk -l to figure out the partition number of the existing EFI partition for MS Windows. mount /dev/sda1 /mnt/boot/efi |
If you want to encrypt boot partition (with GRUB), see here; I did not do it.
Format the partition into filesystems.
-
Mount the partition in which Arch Linux files will be present to /mnt
12mount /dev/mapper/cryptroot /mnt -
Use pacstrap to initialize the Arch Installation If you are behind a proxy server, type: export http_proxy=http://proxy_ip_or_domain:proxy_port
12pacstrap /mnt base <base-devel> -
mount EFI partition
123mkdir -p /mnt/boot/efimount /dev/sda1 /mnt/boot/efi -
Generate the fstab, so that required partitions are mounted on reboot.
12genfstab -U -p /mnt >> /mnt/etc/fstab -
Make sure that /boot and /boot/efi are listed; add them manually if not.
1234567891011121314nano /mnt/etc/fstab---------------------------------------------------# /dev/mapper/cryptboot LABEL=Arch\134x20LinuxUUID=1de833a9-36b8-4bab-91d6-65360080e71c / ext4 rw,relatime,data=ordered 0 1# /dev/sda4UUID=bd82cb16-7b65-4d39-bcca-186edd33bddd /boot ext4 rw,relatime,data=ordered 0 2# /dev/sda1 LABEL=SYSTEM_DRVUUID=4606-2DA8 /boot/efi vfat rw,relatime,fmask=0022,dmask=0022,codepage=437,ioc ...# /dev/sda5 LABEL=Linux\134x20SwapUUID=3c8c0892-f275-485f-9ea5-4f87f34d4e76 none swap defaults 0 0use the following to retrieve UUID:
12345678910ls -l /dev/disk/by-uuid/----------------------------------------lrwxrwxrwx 1 root root 10 May 4 21:57 0C5E30345E3018C2 -> ../../sda6lrwxrwxrwx 1 root root 10 May 4 21:46 12429E3A429E2311 -> ../../sdb3lrwxrwxrwx 1 root root 10 May 4 21:57 12A013A6A0138F7B -> ../../sda5lrwxrwxrwx 1 root root 11 May 4 21:57 1de833a9-36b8-4bab-91d6-65360080e71c -> ../../sda10lrwxrwxrwx 1 root root 10 May 4 21:57 3c8c0892-f275-485f-9ea5-4f87f34d4e76 -> ../../sda9lrwxrwxrwx 1 root root 10 May 4 21:57 4606-2DA8 -> ../../sda1...
How to change LUKS passphrase
The followings are adapted from here.
In LUKS scheme, you have 8 “slots” for passwords or key files. First, check, which of them are used:
|
1 2 |
cryptsetup luksDump /dev/<device> |grep BLED |
Then you can add, change or delete chosen keys:
|
1 2 3 |
cryptsetup luksAddKey /dev/<device> (/path/to/<additionalkeyfile>) cryptsetup luksChangeKey /dev/<device> -S 6 |
As for deleting keys, you have 2 options:
-
delete any key that matches your entered password:
12cryptsetup luksRemoveKey /dev/<device> -
delete a key in specified slot:
12cryptsetup luksKillSlot /dev/<device> 6
Arch and Grub Installation after chroot in.
-
chroot into the arch installation (from live CD).
12arch-chroot /mnt [/bin/bash] -
Configure timezone, generate initial RAM disk. #Chang password for root user
123passwdln -s /usr/share/zoneinfo/America/Los_Angeles /etc/localtime -
Install the bootloader – grub.
Install the packages grub and efibootmgr. GRUB is the bootloader, efibootmgr creates bootable .efi stub entries used by the GRUB installation script.
12pacman -Syu grub efibootmgr [dosfstools]
Generate the main configuration file
-
Make sure all partitions are mounted, i.e. / /boot /boot/efi
1234567891011121314151617mount -alsblk----------------------------------------------------NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTsda 8:0 0 477G 0 disk├─sda1 8:1 0 260M 0 part /boot/efi├─sda2 8:2 0 16M 0 part├─sda3 8:3 0 234.2G 0 part├─sda4 8:4 0 25G 0 part├─sda5 8:5 0 1000M 0 part├─sda6 8:6 0 20.2G 0 part├─sda7 8:7 0 1000M 0 part├─sda8 8:8 0 200M 0 part /boot├─sda9 8:9 0 8G 0 part [SWAP]└─sda10 8:10 0 187.1G 0 part└─cryptroot 254:0 0 187.1G 0 crypt / -
Intial Ramdisk Environment
12mkinitcpio -p linuxAdd the encrypt hook to mkinitcpio.conf: link here
123etc/mkinitcpio.confHOOKS="... encrypt ... filesystems ..." -
update /etc/default/grub
1234GRUB_CMDLINE_LINUX_DEFAULT="i915.preliminary_hw_support=1"GRUB_ENABLE_CRYPTODISK=yGRUB_CMDLINE_LINUX="cryptdevice=UUID=1de833a9-36b8-4bab-91d6-65360080e71c:cryptroot root=/dev$ - install os-prober, only detect the correct Windows boot after boot into Linux, not from chroot with live CD.
-
configure grub
The following steps install the GRUB UEFI application to $esp/EFI/grub, install its modules to /boot/grub/x86_64-efi, and place the bootable grubx64.efi stub in $esp/EFI/grub.
First, tell GRUB to use UEFI, set the boot directory and set the bootloader ID. Mount the ESP partition to e.g. /boot or /boot/efi and in the following change $esp to that mount point (usually /boot):
12# grub-install --target=x86_64-efi --efi-directory=/boot/efi --bootloader-id=grubThe –bootloader-id is what appears in the boot options to identify the GRUB EFI boot option; make sure this is something you will recognize later. The install will create a directory of the same name under $esp/EFI/ where the EFI binary bootloader will be placed.
12grub-mkconfig -o /boot/grub/grub.cfg #Generate initial grub config.Now, let’s add Windows to the GRUB menu. Edit /boot/efi/EFI/grub/grub.cfg and add the following menuentry after the Arch Linux menuentries [Note: grub boot loader does not locate Windows OS, but this is necessary for grub to load Arch Linux in my case. After I boot into arch linux, I ran sudo os-prober and update grub config.] See here for details.
1234567891011if [ "${grub_platform}" == "efi" ]; thenmenuentry "Microsoft Windows Vista/7/8/10 UEFI-GPT" {insmod part_gptinsmod fatinsmod search_fs_uuidinsmod chainsearch --fs-uuid --set=root $hints_string $fs_uuidchainloader /EFI/Microsoft/Boot/bootmgfw.efi}fiand update the string with following output:
$latex hints_string with the output of $ grub-probe –target=fs_uuid /boot/efi/EFI/Microsoft/Boot/bootmgfw.efi $latex fs_uuid with the output of $ grub-probe –target=hints_string /boot/efi/EFI/Microsoft/Boot/bootmgfw.efi
Unmount and Reboot
|
1 2 3 4 |
exit umount -R /mnt reboot |
Finish Up Arch Linux Installation
- Install the desktop environment, display manager, and vim and xterm. packman -Syu gnome-desktop xterm vim gnome-display-manager systemctl enable gdm #Start gdm on boot
- Create a new user and add him to the group wheel. useradd -G wheel -s /bin/bash -m -c “Nehal J Wani” wani passwd wani
- Reboot into Arch Linux
-
Install os-prober. Regenerate grub configuration. Reboot.
12345pacman -Syu os-probersudo os-prober#/dev/sda1@/EFI/Microsoft/Boot/bootmgfw.efi:Windows Boot Manager:Windows:efigrub-mkconfig -o /boot/grub/grub.cfgDone! Now you can choose between Windows and Arch Linux at the start. Yay!
Install Arch Linux
-
Retrieve package list from another system To create a list of all official repository installed packages do:
12$ pacman -Qqe | grep -v "$(pacman -Qqm)" > /mnt/backup/pkglist-off.txtTo create a list of all local installed packages do (includes packages installed from the AUR):
12$ pacman -Qqm > /mnt/backup/pkglist-loc.txt -
install package in new system To reinstall packages using the backup package list:
123pacman --needed -S - < /mnt/backup/pkglist-off.txt#use pacaur or yaourt for local packages - Restore configuration with instruction here (use rsync with -a to mantain symlinks).
-
install python modules
123pip freeze > pipfile #populate listpip install -r pipfile -
install node.js modules
123npm list -g --depth=0 >npm #orls `npm root -g` >npm-global -
The new system
Some further tweaks
Wifi fix
|
1 2 |
modprobe –rfv ideapad_laptop #needed for internet connection |
Next is to make sure that we unblock hw killed wifi due to the above module
|
1 2 3 4 5 6 |
rfkill –list rfkill unblock all modprobe –rfv iwlmvm modprobe -fv iwlmvm wifi-menu |
/etc/modprobe.d/blacklist.conf
|
1 2 3 4 |
Add the following lines blacklist ideapad_laptop blacklist nouveau |
Customize Grub
install grub-customizer with pacman, and customize grub loader
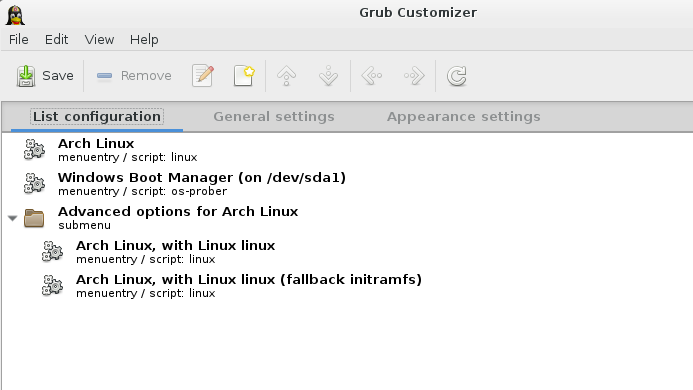
starfield theme is chosen here.
Bumblebee Switch the Graphics Card
Bluetooth
Encrypting a non-root file system
You can encrypt a secondary filesystem from a partition to protect only sensitive data. The following shows how to create a common partition for all user’s /home directories.
-
First, make sure the partition is empty (has no file system attached to it). Delete the partition and create an empty one if it has a file system.
Create the partition which will contain the encrypted container.
-
Then setup the LUKS header with the following:
12# cryptsetup options luksFormat deviceReplace device with the previously created partition.
To gain access to the encrypted partition, unlock it with the device mapper, using:
12# cryptsetup open device nameAfter unlocking the partition, it will be available at /dev/mapper/name. Now create a file system of your choice with:
12# mkfs.fstype /dev/mapper/name - Mount the file system to /home, or if it should be accessible to only one user to /home/username Tip: Unmount and mount once to verify that the mapping is working as intended.
-
To mount the partition manually:
123# cryptsetup open device name# mount -t fstype /dev/mapper/name /mnt/home -
To unmount it manually:
123# umount /mnt/home# cryptsetup close name
Mount at boot automatically
-
generate key file
12345# cryptsetup luksAddKey /dev/<device> -S 6Enter any passphrase:Enter new passphrase for key slot:Verify passphrase: -
create crypttab If the keyfile for a secondary file system is itself stored inside an encrypted root, it is safe while the system is powered off and can be sourced to automatically unlock the mount during with boot via crypttab. For example, unlock a crypt specified by UUID:
123/etc/crypttabhome-crypt UUID=UUID-identifier /etc/mykeyfile -
then add it to fstab Then use the device mapper’s name (defined in /etc/crypttab) to make an entry in /etc/fstab:
123/etc/fstab/dev/mapper/home-crypt /home ext4 defaults 0 2
MAR

About the Author:
Beyond 8 hours - Computer, Sports, Family...